
Future-Proof IT Support Made Strategically Simple
Secure, Manage, and Scale Your Business Technology with Confidence.

Secure, Manage, and Scale Your Business Technology with Confidence.
Your business operates as efficiently and securely as the technology supporting it. When your IT systems perform seamlessly, they ensure safety, speed, and productivity, empowering your team to meet deadlines and drive growth effectively.
But what happens when things go wrong?
- Sluggish internet leading to productivity bottlenecks
- Limited access to work when tied to office computers
- Heightened exposure to cybersecurity threats
- Frustrated employees struggling to complete tasks
- Valuable time lost waiting for tech issues to be resolved
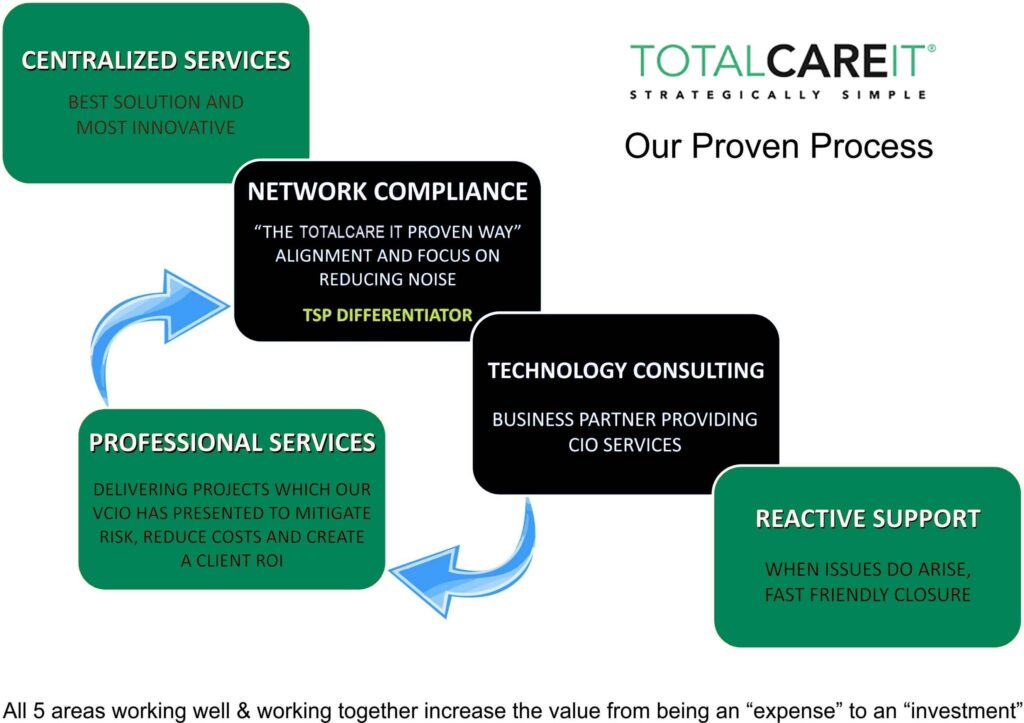
Efficient IT Management and Support Services Designed to Drive Business Growth
Harness enterprise-level technology management solutions tailored to your needs—at a price designed for small businesses.
Cybersecurity
Protect your business from evolving threats with advanced, proactive cybersecurity measures tailored to safeguard your sensitive data.
Managed IT
Streamline your operations with fully managed IT solutions, designed to keep your business running efficiently and securely.
Co Managed IT
Collaborate with your internal IT team by leveraging our expertise and resources to enhance your current capabilities.
Cloud Computing
Empower your business with scalable, secure cloud solutions that enhance flexibility, collaboration, and storage efficiency.
Save Time
Spend more time ensuring your customers are satisfied and scaling your business
Increase Productivity
Let outsourced IT take care of your tech needs while you spend time on your business
Lower Risk
Not just lowering the expense of a breach or lost productivity from the same issues over and over again, but the operational maturity of a company using a process that guarantees results.
Maximize Your Technology's Revenue-Boosting Potential
While owning your own business offers the freedom to be your own boss, many entrepreneurs find themselves overwhelmed, taking on too many responsibilities, and losing the freedom they once sought.
Stop wasting time and money navigating your IT challenges.
Let Total Care IT provide tailored technical solutions, allowing you to focus on growing and running your business efficiently.
Testimonials
As an owner of NSI Radiology, I know we are a highly tech-dependent company. With multiple locations in Florida, we found that in-house IT could easily be compromised should something horrible happen to any of the people in IT. We needed documentation of our complex network and processes for support delivery and to ensure our customers continued receiving our exceptional service. We turned to TotalCareIT and found them to be highly competent, responsive, and able to handle any task, no matter how difficult. I would highly recommend them to anyone to enhance an IT department. We are happy to have a scalable process in place to enjoy being Brevard’s highest-quality imaging center.

TotalCareIT has delivered fast reliable support since 2003. They manage our Cisco Unified Communications, our network servers and desktops. The have performed numerous reliable upgrades to our software and hardware over the years with attention cost and uptime. In 2010, their disaster recovery implementation allowed us to continue to do business when our server crashed. I can sleep at night knowing that when I come in on a Monday morning it will be business as usual.

Due to an unexpected turn of events, we found ourselves in quick need of outsourcing our IT requirements. We were referred to Charles at TotalCareIT; he and Mark quickly jumped into action and seamlessly incorporated what was needed to secure our backup procedure and system updates. Any problems that occurred were dealt with in a swift and effortless manner. ABS Structural Corporation would strongly recommend TotalCareIT for your business’s technology service needs.

TotalCareIT took over our complex network when our internal IT guy left 10 years ago. They started off by documenting the network and then swiftly made dramatic changes to simplify our infrastructure. I really thought they would just manage what we had as it was in their best interest financially. We really haven’t trusted IT before this as just operated like it was an exaggerated cost of doing business in our industry. They actually lower our operational cost, and provided a higher level of reliability. When we had issues they had support onsite the same day. We really felt like they understood how important uptime was to us (and how much downtime cost us). They continue to impress me and my employees by going above and beyond to make sure my business stays connected 24/7. Our business has grown dramatically since those days and TotalCareIT has been there to guide us to the business results we need to maintain our rapid expansion. Don’t tell anyone else about them, so we can keep them all to ourselves.

Our company has been using TotalCareIT for over 10 years. They have done a great job navigating us through our growth and the IT needs that have come with it. TotalCareIT also has done an amazing job jumping right on things when we have had IT issues so that any business interruptions were minimized. Charles Berry and his team do a great job communicating and we are very happy clients.

Top Rated
Service 2025
Your IT Solution is Just 3 Steps Away
Schedule a Quick Call
Begin with a non-technical, strategic discussion to help us fully understand your current IT situation. This conversation allows us to align our approach with your unique needs and goals, setting the foundation for effective, tailored IT solutions.
Get A Custom Roadmap
Our team will design a tailored action plan to demonstrate what optimized IT looks like for your organization. This roadmap outlines strategic steps to elevate your technology, streamline operations, and support your team's success.
Experience Better IT
We’ll manage a smooth transition to our IT services, ensuring minimal disruption and no hassle for your team. With clearly defined metrics for success, we’ll monitor progress and keep your IT running optimally, so you can stay focused on your core business.

Proven Success: 98% Client Satisfaction
At TotalCareIT, we recognize the essential role technology plays in your company’s growth.
Picture a scenario where:
- Your IT challenges are swiftly resolved by a team that understands your business inside and out.
- You have access to friendly, expert support around the clock, wherever you are.
- You can rest easy knowing your IT systems are managed by trusted professionals.
Ready to leverage technology for your business growth?
Contact us today for a free technology assessment and get the insights you need to tackle your network and security challenges.