
Future-Proof IT Support Made Strategically Simple
Secure, Manage, and Scale Your Business Technology with Confidence.

Secure, Manage, and Scale Your Business Technology with Confidence.
Your business operates as efficiently and securely as the technology supporting it. When your IT systems perform seamlessly, they ensure safety, speed, and productivity, empowering your team to meet deadlines and drive growth effectively.
But what happens when things go wrong?
- Sluggish internet leading to productivity bottlenecks
- Limited access to work when tied to office computers
- Heightened exposure to cybersecurity threats
- Frustrated employees struggling to complete tasks
- Valuable time lost waiting for tech issues to be resolved
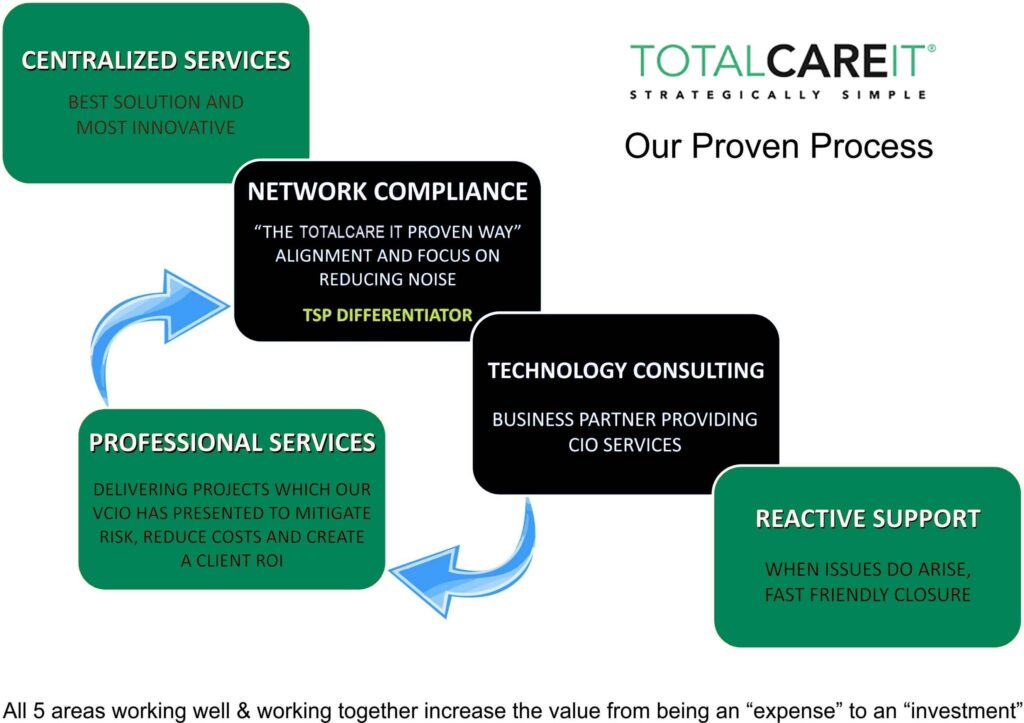
Efficient IT Management and Support Services Designed to Drive Business Growth
Harness enterprise-level technology management solutions tailored to your needs—at a price designed for small businesses.
Cybersecurity
Protect your business from evolving threats with advanced, proactive cybersecurity measures tailored to safeguard your sensitive data.
Managed IT
Streamline your operations with fully managed IT solutions, designed to keep your business running efficiently and securely.
Co Managed IT
Collaborate with your internal IT team by leveraging our expertise and resources to enhance your current capabilities.
Cloud Computing
Empower your business with scalable, secure cloud solutions that enhance flexibility, collaboration, and storage efficiency.
Save Time
Spend more time ensuring your customers are satisfied and scaling your business
Increase Productivity
Let outsourced IT take care of your tech needs while you spend time on your business
Lower Risk
Not just lowering the expense of a breach or lost productivity from the same issues over and over again, but the operational maturity of a company using a process that guarantees results.
Maximize Your Technology's Revenue-Boosting Potential
While owning your own business offers the freedom to be your own boss, many entrepreneurs find themselves overwhelmed, taking on too many responsibilities, and losing the freedom they once sought.
Stop wasting time and money navigating your IT challenges.
Let Total Care IT provide tailored technical solutions, allowing you to focus on growing and running your business efficiently.
What Our Clients Say
EXCELLENTTrustindex verifies that the original source of the review is Google. Always and consistently helped with issues and they are promptly addressed and solved. I'm always happy with the experience.Posted onTrustindex verifies that the original source of the review is Google. Amazing support , always ready to assist , professional, patience, knowledgeable, and kind....Thanks guy's for being so efficient!!!!Posted onTrustindex verifies that the original source of the review is Google. Working with Charles Berry at Total Care IT in Melbourne Fl has been a pleasure. He is extremely knowledgeable in the IT Industry including Managed IT and Cyber Security. If your business is looking to take security to the next level then I definitely recommend giving them a call. Thank You Charles!Posted onTrustindex verifies that the original source of the review is Google. I have been a client of Total Care IT for almost fifteen years and while that speaks volumes I will add that these guys are top shelf. Their knowledge, patience with less IT inclined clients, and customer service is excellent. In all the years we have been with Total Care we have had minor security issues that were always resolved quickly and without internal disruptions or compromised data. We love Total Care IT!!Posted onTrustindex verifies that the original source of the review is Google. Easy to contact, timely and proper resolutions to issues.Posted onTrustindex verifies that the original source of the review is Google. Great company!! Shorty is amazing!! Resolves issues efficiently and professionally and provides insight for increased performance!! Thank you, Shorty and the TotalCareIT Team!!Posted onTrustindex verifies that the original source of the review is Google. TotalCareIT is very responsive, respectful, and helpful when it comes to customer service! They helped me a lot with my IT needs for my business structure, especially Charles Berry! He explained everything to me to where I could understand it and helped every step of the way. Thankful for companies like this.Posted onTrustindex verifies that the original source of the review is Google. The Best
Your IT Solution is Just 3 Steps Away
Schedule a Quick Call
Begin with a non-technical, strategic discussion to help us fully understand your current IT situation. This conversation allows us to align our approach with your unique needs and goals, setting the foundation for effective, tailored IT solutions.
Get A Custom Roadmap
Our team will design a tailored action plan to demonstrate what optimized IT looks like for your organization. This roadmap outlines strategic steps to elevate your technology, streamline operations, and support your team's success.
Experience Better IT
We’ll manage a smooth transition to our IT services, ensuring minimal disruption and no hassle for your team. With clearly defined metrics for success, we’ll monitor progress and keep your IT running optimally, so you can stay focused on your core business.

Proven Success: 98% Client Satisfaction
At TotalCareIT, we recognize the essential role technology plays in your company’s growth.
Picture a scenario where:
- Your IT challenges are swiftly resolved by a team that understands your business inside and out.
- You have access to friendly, expert support around the clock, wherever you are.
- You can rest easy knowing your IT systems are managed by trusted professionals.
Ready to leverage technology for your business growth?
Contact us today for a free technology assessment and get the insights you need to tackle your network and security challenges.